Knowing what types of penetration tests exist is the first step to finding a solution that suits your needs, especially in a world where cybersecurity is becoming increasingly important.
To learn more about what penetration testing is, read our article.
In this editorial, we will delve into the various types of Penetration Tests that exist:
-
Target
-
Methodologies
Penetration tests differ from each other based on various factors, such as the type of infrastructure being attacked, the type of information provided to testers beforehand, etc.
Additionally, different tests can follow different penetration testing methodologies and frameworks, each leading to different methods, timelines, and results.
What are the targets of a Penetration Test?
As mentioned earlier, the purpose of a penetration test is to uncover system vulnerabilities and assess the severity of the risks involved.
The pentest process can vary significantly in terms of methods, duration, and approaches used; these factors largely depend on what is being attacked.
Given the diverse modes and areas of interest, penetration tests have diversified and specialized to achieve the best results in a specific field.
Today, there are different types of penetration tests that focus on different targets:
Network pentest
Tests aimed at verifying the security of a network.
This pentest is particularly important for two reasons: first, it concerns the vast majority of security aspects within a company, and second, network attacks are becoming increasingly sophisticated.
The network penetration test focuses on the security of networks, hosts, and devices.
Network penetration tests can be of type:
External, if they pass through servers (websites, mail servers, etc.) or network devices accessible from the internet - This type of test is useful for assessing the impact of attackers who do not have physical or remote access to the corporate network.
Internal, if the test is conducted within the corporate network, either physically or through remote connections. The attack is aimed at discovering the risks if a malicious actor gains access to the network. This type of testing is particularly useful if employees are allowed to bring personal electronic devices into the company (BYOD policy).
Malware on personal devices can spread across the network and compromise it.
Web application pentest
This is a penetration test to discover vulnerabilities and assess security in classic web applications or single-page apps.
This type of test is specific but extremely broad, especially regarding attack vectors. Security flaws in a website can hide in the software logic itself, in the use of user inputs that are not properly checked, in the use of outdated components, or in insecure configurations.
Specific details on web application penetration testing can be found in the manual offered by OWASP, available online for free at: https://www.owasp.org/images/1/19/OTGv4.pdf
Mobile app pentest
This testing aims to find security flaws in mobile applications. Mobile application penetration testing is a relatively new mode and focuses on several well-defined key points:
the quality of the implemented client-server architecture;
the security of data stored on the device;
the verification of secure communications;
the security of authentication;
the security of the server platform;
the presence of vulnerabilities in the API code and backend services used by the application.
An application can be attacked from different fronts, and making it secure is a complex task. OWASP is developing the Mobile Security Testing Guide, a manual for secure mobile application programming and related penetration testing.
The first version is available at: https://mobile-security.gitbook.io/mobile-security-testing-guide/
API Penetration Test
APIs (Application Programming Interfaces) are the way software interfaces with a server.
APIs are extremely common and widely used, which is why the security of this tool is crucial.
A hacker could potentially abuse the APIs provided by the server to perform malicious actions, access sensitive data, or compromise the service.
For this reason, if APIs are implemented, whether public or for private use, it is essential to secure this interface accessible to anyone on the web.
During the API penetration test process, it is verified that the application's logic works correctly, especially regarding authentication and authorization mechanisms. Additionally, it is carefully checked if and how the code sanitizes input, a crucial step for assessing the presence of "injection" attacks.
OWASP has dedicated a project to API security, highlighting the 10 most common vulnerabilities and explaining how to test for these vulnerabilities and how to fix any issues. The project is available at: https://owasp.org/www-project-api-security/
IoT Penetration Test
Penetration testing of IoT (Internet of Things) infrastructures is becoming an increasingly requested practice. IoT devices are now everywhere, from the automotive sector to healthcare, personal use, and businesses.
The IoT penetration test focuses on finding security flaws in the operation of these infrastructures to extract information or compromise their functionality.
IoT devices are tested to find vulnerabilities such as:
Weak, "hard-coded," or easily guessable passwords
A common vulnerability on IoT devices, often default passwords are maintained, or maintenance accounts with passwords specified in the code and therefore not modifiable are left active;
Insecure services made publicly available, such as dashboards or diagnostic tools;
Issues with the IoT ecosystem, such as insufficient authorizations and authentications or insecure logic between back-end and devices.
Device update mechanisms are also checked to ensure they are secure, as well as insecure configurations or physical security of the devices.
Although there are different targets, these are not mutually exclusive. In fact, a comprehensive penetration test requires evaluating all security aspects of an infrastructure, including, of course, all relevant targets.
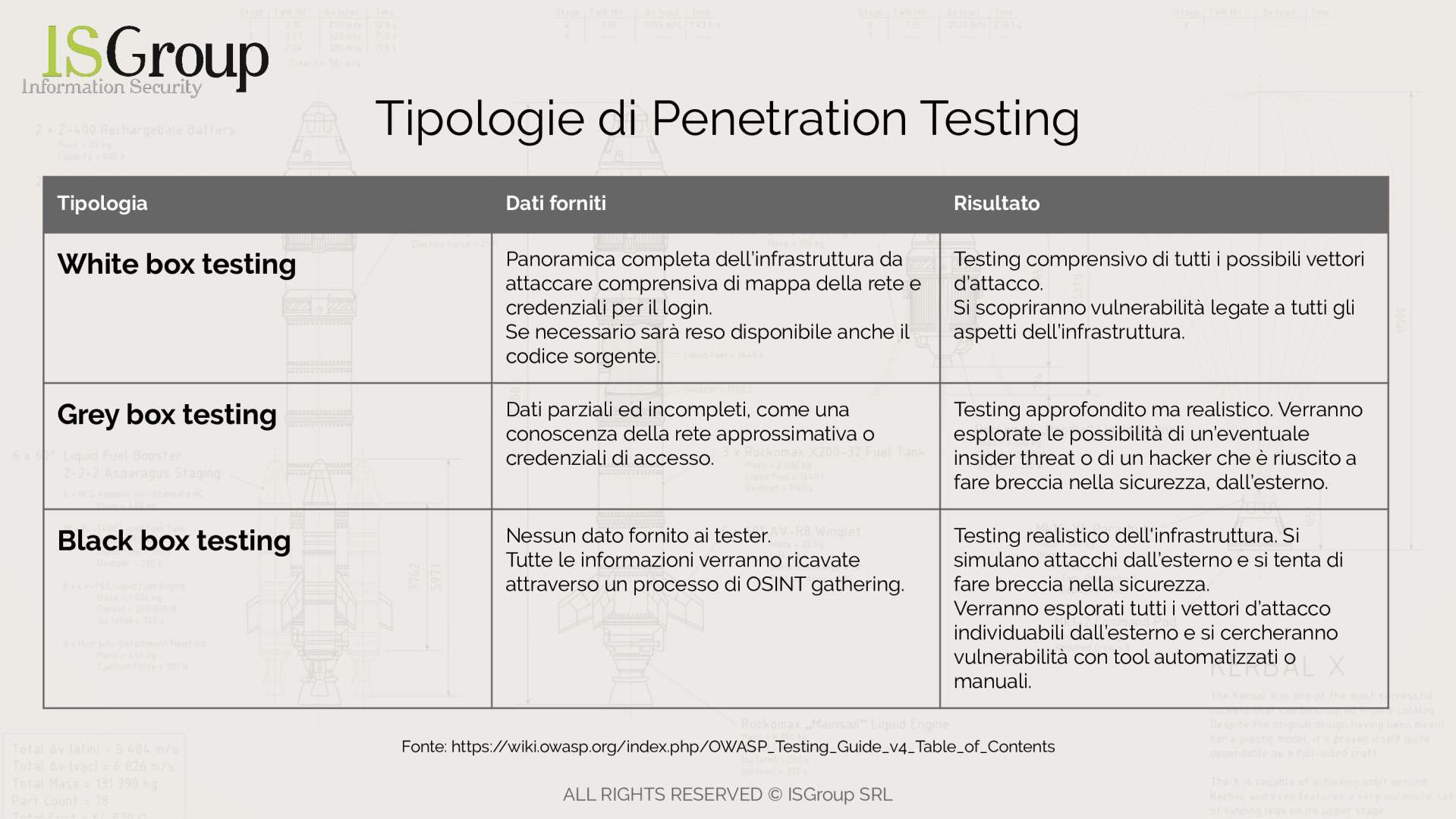
Penetration testing White Box, Grey Box, or Black Box?
Penetration tests are not classified solely based on the targets they test, but also on the level of knowledge the testers receive about the system before starting.
Although the knowledge of an infrastructure is better represented on a spectrum rather than in distinct classes, testing is divided into three different types: White box penetration testing, Black box penetration testing, and Grey box penetration testing.
White box penetration testing
The penetration tester has received detailed information about the target and infrastructure, such as a network map and access credentials useful for conducting the tests.
White box penetration testing is an assisted mode of scenario simulation. Thanks to the information provided to the tester, such as documentation, architecture design, and source code, it allows for greater coverage and provides an extensive overview of every possible attack vector.
Although white box penetration testing saves time initially (as there will be no need for a reconnaissance phase), it can still be very time-consuming due to the numerous attack vectors that penetration testers will need to evaluate and test.
Black box penetration testing
A scenario diametrically opposed to white box penetration testing. Testers are not provided with any information about the infrastructure to be attacked.
The penetration tester will play the role of an attacker attempting to compromise the security of the infrastructure from the outside. This type of testing is useful for modeling an external attack, which is the most plausible and common.
Black box penetration testing will require evaluating attack vectors accessible from the outside. It is important to keep in mind that although this attack can model specific situations, it does not offer a complete security overview because the tester will not have the opportunity to examine all possible attack vectors.
Grey box penetration testing
In this scenario, penetration testers are provided with only partial information, usually login credentials. Grey box penetration testing allows modeling situations where a hacker from the outside has gained access to the internal network, or to simulate an insider threat.
Grey box penetration testing is a middle ground between white box and black box, making it useful for realistically testing security without delving into overly detailed tests.
Typically, grey box testing is the preferred choice if there are no specific needs and if a sufficiently comprehensive security overview is desired.
Conclusions
Before starting the penetration testing process, it is important to understand which type of testing best suits your needs in terms of security assessment, timelines, and costs.
Below is a table that briefly summarizes the types of testing available to choose from.