As the name immediately suggests, the Purple Team is the derivation and union between the Blue Team and the Red Team, permanent teams within the company to manage Cybersecurity.
Cybersecurity represents a fundamental sector in the control and safeguarding of networks, applications, and websites in both civil and military contexts.
In this editorial, we will delve into the aspects of the Purple Team in Cybersecurity:
What is the Purple Team?
The most important and renowned teams in the field of cybersecurity have always been the "Red Team" and "Blue Team", probably the first colors and respective teams to appear in cybersecurity.
Clear division and competition between the two teams were the order of the day until someone thought that creating a bridging team would bring evident advantages to both teams and, above all, a better final result.
The main role of the purple team is indeed to supervise and optimize the work and communications that occur between the Red Team and the Blue Team.
This allows for better communication, better penetration testing, and related defense, and in general, a more collaborative culture through the "mediating" function generated by the purple team.
The Purple Team for cost optimization
Thanks to the work of the Purple Team, it is possible to have an initial and accurate overview of the Cybersecurity system to be tested. Then, if there is a need to delve deeper into certain details, a Red Team and a Blue Team can be engaged for an in-depth test.
In this way, costs can be optimized because the two teams would only face each other in certain areas, namely those where the Purple Team has not achieved a real success.
Similarly, especially in relation to more extensive and complex IT systems, the Purple Team is able to perform an initial "screening", that is, to establish the weak points that require an in-depth analysis.
Once these are identified, the Red Team and Blue Team can intervene with their respective tasks.
Purple Team vs Blue Team vs Red Team
Let's make a brief summary to better understand what the purple team is for and why it was created.
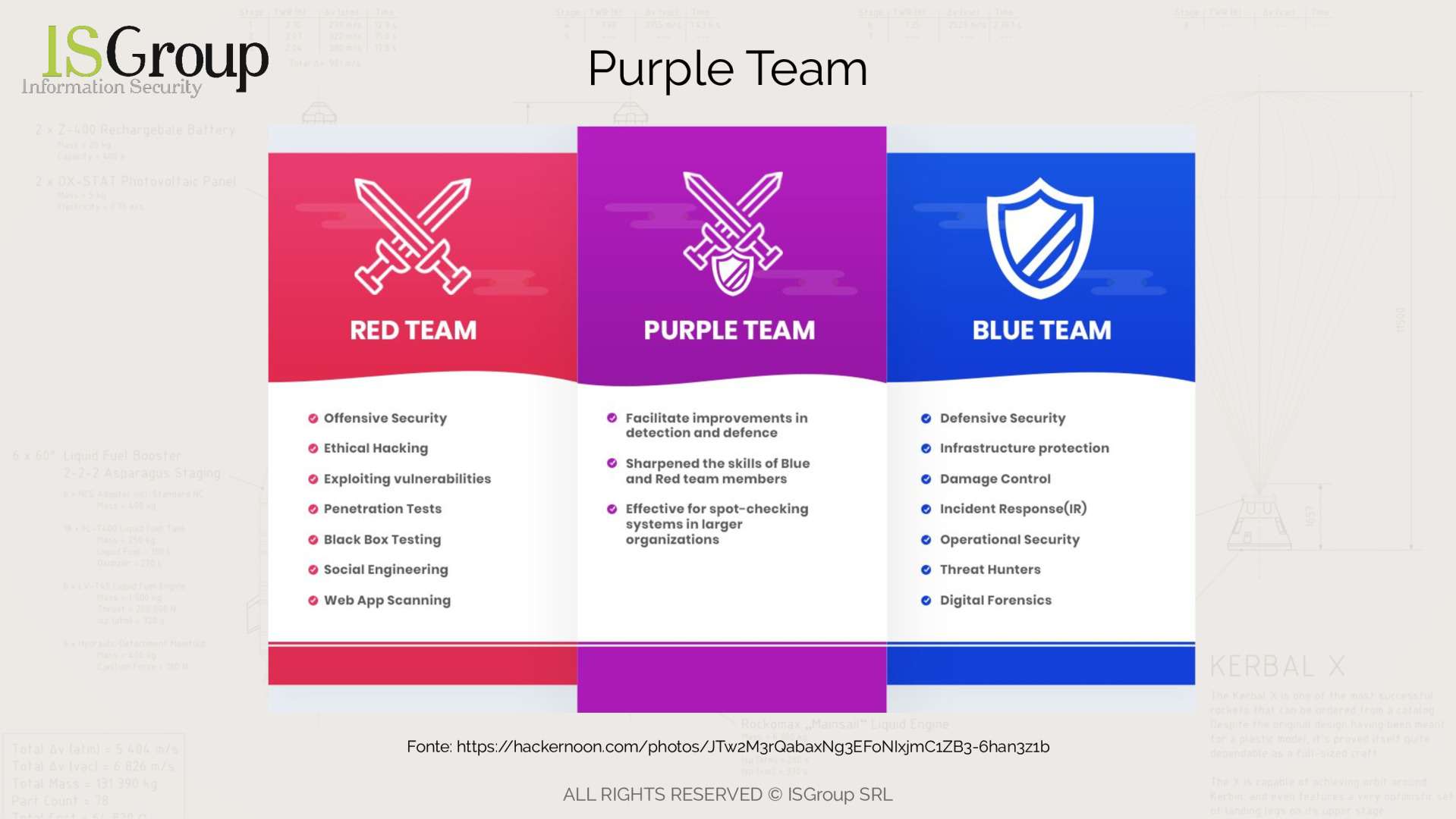
Red Team
The red team is usually composed of "ethical hackers" whose goal is to break into the system.
An often independent team hired by companies to put the system "under pressure", find and highlight vulnerabilities, in order to solve critical issues before a malicious attacker can exploit any system flaws.
The red team works with well-defined objectives, which consist of infiltrating the system, deceiving defense systems and the people assigned to them (the defenders, the blue team).
The red team looks for loopholes, bugs, and crevices to exploit to enter the corporate system and carry out malicious actions.
On the other side of the "battlefield", there is someone who works tirelessly to prevent these actions, through prevention and protection work (the blue team).
Blue Team
The counterpart and nemesis of the red team is the blue team.
The blue team is usually an internal team within the company, grouped in a "SOC", Security Operations Center.
This team is composed of qualified analysts, whose main task is the defense of the infrastructure.
Defense that they normally achieve in two ways:
-
Preventively, through the creation of barriers, protections, and even "baits" to safely divert the attack to a desired "place" from the outside.
-
Reactively, to intervene when needed, when the attack perpetrated is too sophisticated, innovative, or varied to be detected and fought by automatic protection systems and human intervention is necessary.
The blue team is the one that tries to educate operators in the company, makes them change passwords periodically, etc...
The blue team does not perform these actions (and many other "invisible" ones to the average employee) without a purpose, its goal is indeed to minimize and reduce the risk of IT breaches to zero, through clear and well-defined procedures.
Attackers vs defenders then?
Yes, but since the world is not just black and white, there was a need for a link between the two groups, a solution that would bring advantages to everyone, a bridge between the two teams, a mediation unit.
Hence the birth and creation of the purple team, a new approach, a combination of these two teams (and colors) that stands in the middle between the two, bringing advantages to both and to the system in general.
The purpose of the purple team members is indeed to supervise the work carried out by the Red Team and Blue Team, trying to make them communicate better in function of the shared final goal.
Purple team
Now that we have discovered how this team was born, let's better understand what the activities of the purple team are and who composes it.
The purple team is usually composed of security analysts (Senior Security Analysts) and threat analysts (Threat Intelligence Analysts).
Union from the two teams from which it is derived (although typically composed mostly of personnel from the red team), the purpose of this team is mainly communicative and supervisory.
It indeed allows maintaining competition within the bounds of utility, ensuring that communication remains within the required scope, is linear and shared.
Another fundamental characteristic of the purple team is flexibility.
The purple team is indeed a non-permanent team, but created from time to time based on the need to be verified and the behavior of the two teams from which it is derived.
This allows the purple team to always be "fresh" and with new ideas and suggestions.
Purple team activities
The activities of the purple team add value in the phases of IT security testing.
When there is a need to perform an "attack automation" or a "Penetration Test", it is always good to create a purple team in advance or try to make it emerge from the joint work of the Red Team and Blue Team.
The purple team facilitates communication between the two teams, collects useful data and information for subsequent tests, and analyzes the results in real-time.
The work of the purple team is also to "guide" the Red Team, giving it suggestions for attack areas, in order to test a new protection, a possible flaw, or a trap prepared by the blue team.
On the other hand, conversely, the purple team can help the Blue Team understand how the attack is being perpetrated and manage it in the best way.
Moreover, the purple team has the fundamental, albeit unwritten, function of referee and supervisor with an important role in verifying compliance with the conditions of the challenge and respect for the teams and their respective skills and tasks.
Why does a company need a purple team?
Having a Red Team and a Blue Team without a buffer in the middle could prove detrimental in the short term.
Without a purple team, the two teams from which it is derived will never confront each other.
The Blue Team will not help the Red Team in the slightest; the goal of the former is the absence of threats or their rapid control; so why help the enemy?
The Red Team, on the other hand, will not interact with the Blue Team at all.
In a competitive condition, it will indeed try to create the "greatest possible damage".
The creation of the purple team allows the competition to level up, removing egos and childish failures in favor of an implemented and functioning cybersecurity.
In addition to communication and collaboration, the purple team can bring other advantages to the company and its IT security.
Why insist on the importance of the purple team
The adoption of a purple team can lead to a significant reduction in feedback and implementation times of what has been discovered and identified by the red team.
This team indeed allows the abolition of the compartmentalized logic, ensuring a constant flow of information; a condition that allows for real-time work correction.
The facilitation of attack procedures allows the "immediate" construction of the most correct defense system.
The sharing of the defensive procedure allows, in an opposite way, the Red Team to better understand the playing field and to test weaknesses and possible entry points that they might not have thought of yet.
Some examples of successful adoptions
The adoption of the purple team logic has met with immediate success from the largest companies in the sector.
Intel created its first purple team in 2007 and still "exploits" it daily.
Google, Microsoft, Oracle, and other big names in IT and cybersecurity have permanent purple teams or create them as needed in various testing and control phases.
Even "less" technological companies, such as the North American distribution giant WalMart, have created a purple team that they use daily for the control and implementation of their IT system.
Conclusions
The IT security of your structure assumes greater critical importance every day.
Just as in the medical system, viruses and bacteria become more intelligent and performing every day, the same happens for IT threats.
Therefore, your defense system must also evolve every day.
Like every battle, communication is often what can lead to the final victory in the long term; especially when the challenge is between two armies that, although opposed, have the same final goal.
Speed and readiness of response in the field of cybersecurity are everything, the implementation of a purple team allows for a significant reduction in communication and feedback times, avoiding updates and conclusions only at the end of the exercise, but introducing them in real-time.



